第一次撿到野生的 Malware。
先講結論!由於時間有限以及本人的技術不到位,最後並沒有很理想的結果。
希望之後在 Malware Analysis 這塊技能樹點起來再回來分析會有所成長 QQ

Story Time
前回提要
我校為了提升校園網路環境安全,在今年初針對外對內的 RDP、FTP、SSH、MS-SQL、TELNET 藉由 IPS 通通擋掉。而我們 Lab 主要運作的伺服器由於有連線的需求而向學校申請 IP 連線許可,在疫情被迫 Work From Home 的非常時期顯得相當重要。
而最近,我們 Lab 收到了校方的資安通報,而目標 IP 正是主要運作的伺服器,據說是中了蠕蟲。
雖然我認為做為資安相關研究應該要收個資安通報解解成就,但是這次實在是莫名的讓人措手不及,這幾天分別由 @stavhaygn 和 @hanhan3927 學長兩位網管(?)負責調查,從假日看到他們螢幕上滿滿的 log,真的很辛苦呢。
而在今天 @stavhaygn 在群組丟了兩隻 Malware 問我有沒有興趣分析,起初我只是抱著難得有機會加減摸一下(順便把生灰塵的 Parallel Desktop 拿出來清),結果拿去餵 VirtualTotal 發現是一種蠕蟲,很自然地就想到前陣子的資安通報。
很明顯事情並沒有照著劇本走,因為 Lab 主要運作的伺服器是 Linux,而撿到兩隻的 Malware 都是 .exe 完全不能執行(用紅酒除外),第一時間還很不識相的在群組出聲,哭啊被嘲諷 QwQ

故事大概就這樣,
下面會分享第一次分析 Malware 我做了哪些事,以及用到哪些工具(即便我都不熟==)。
Simple Analysis
PeStudio
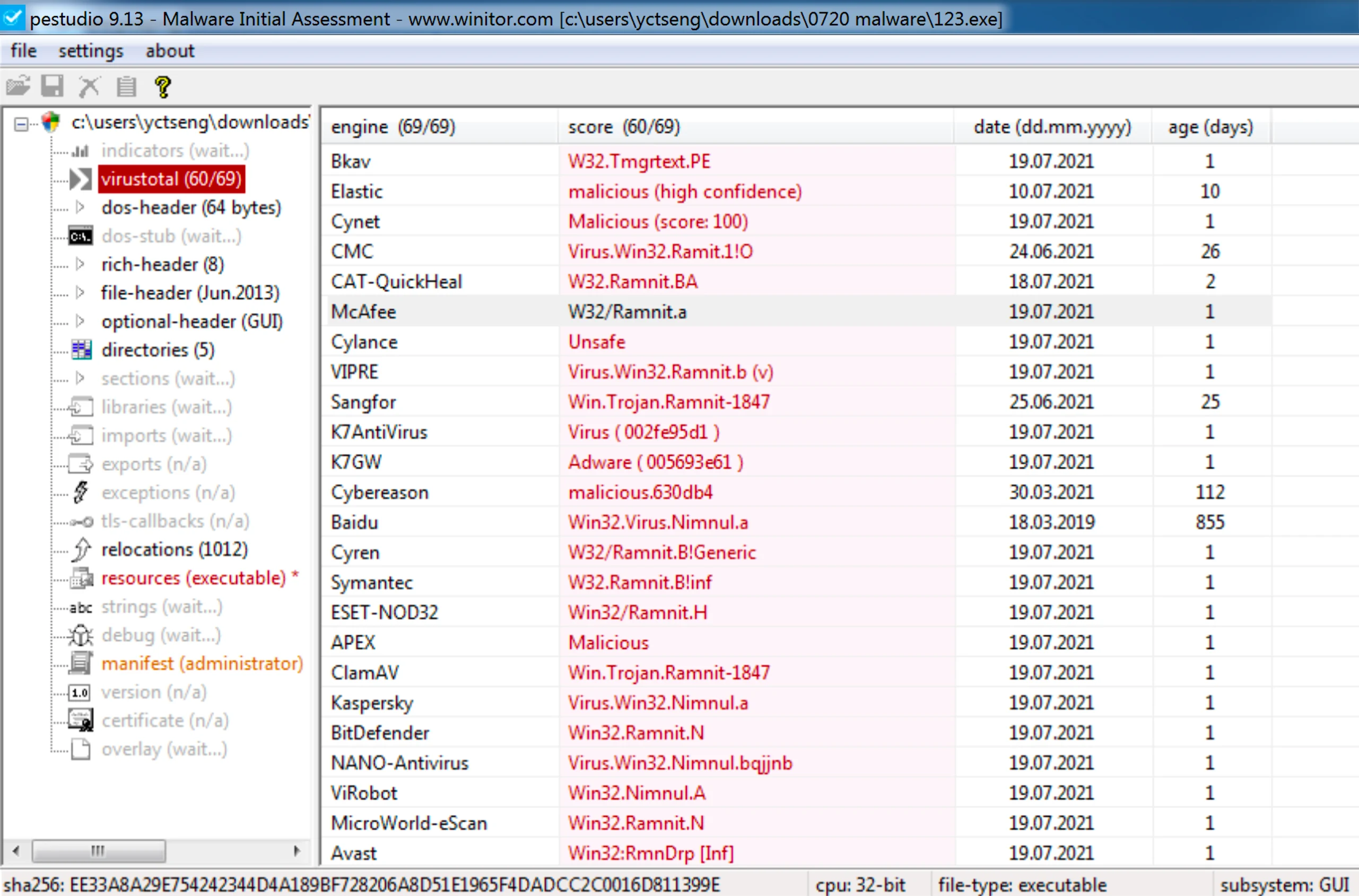
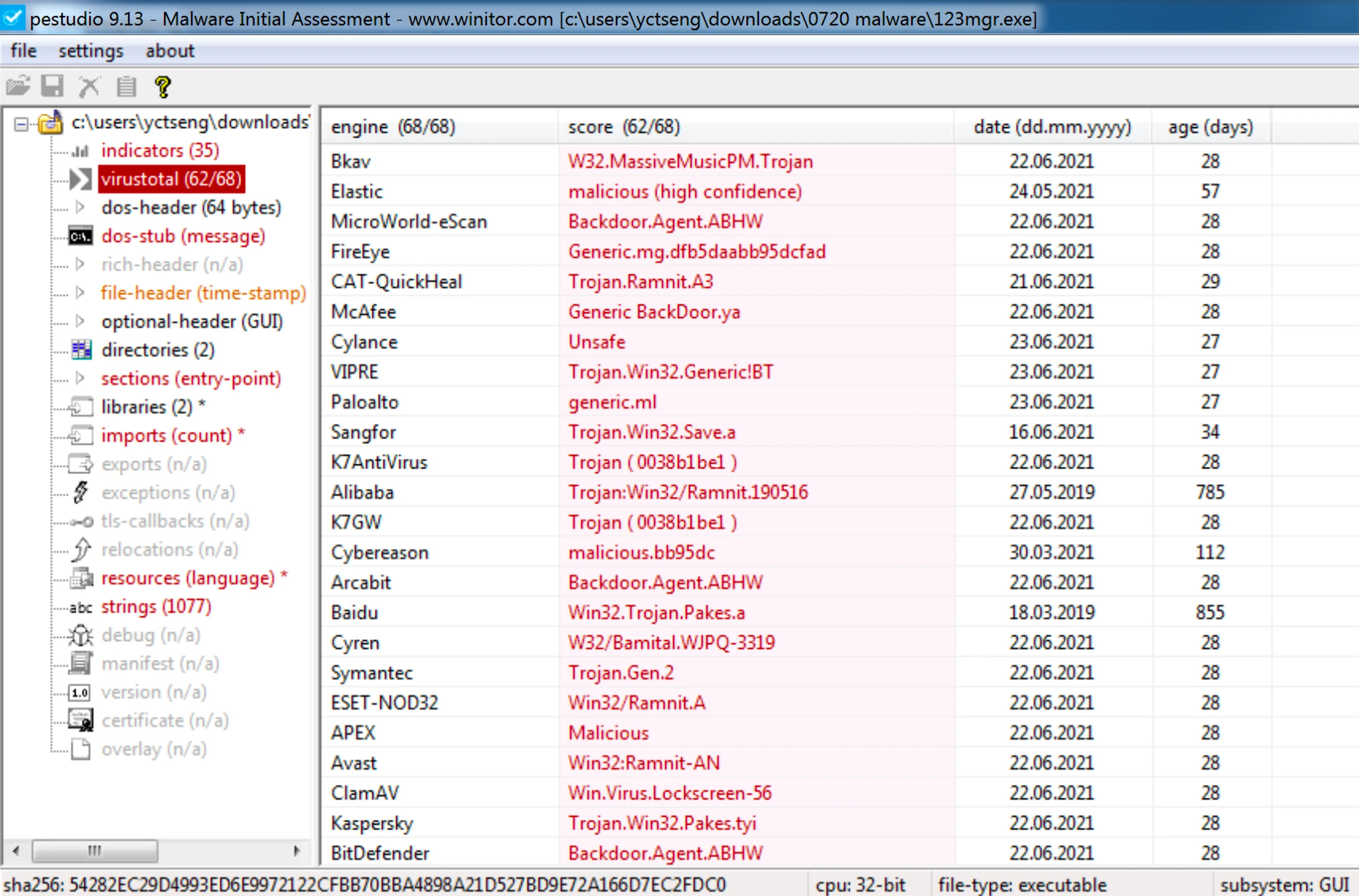
附上兩隻 Malware 在 VirusTotal 的結果,這裡使用 PeStudio 做為分析 .exe 的起手式,可以看到兩者皆為 32-bits 以及右圖 Malware 有加殼(UPX) 等等檔案資訊。


從之後的研究可知兩者為前後關係,分別是由左圖的 malware-A 執行後產生副產物 malware-B。
VirusTotal 的結果分別為 malware-A (60/69)、malware-B (62/68),而 malware-A 被大部分防毒軟體判讀出來的 Ramnit 是當前臺灣企業受駭最多的一種惡意攻擊手法(iThome 新聞),網路上也不難找到相關的分析報告,接下來我想了解的就是這組 Malware 到底做了什麼。
IDA Pro
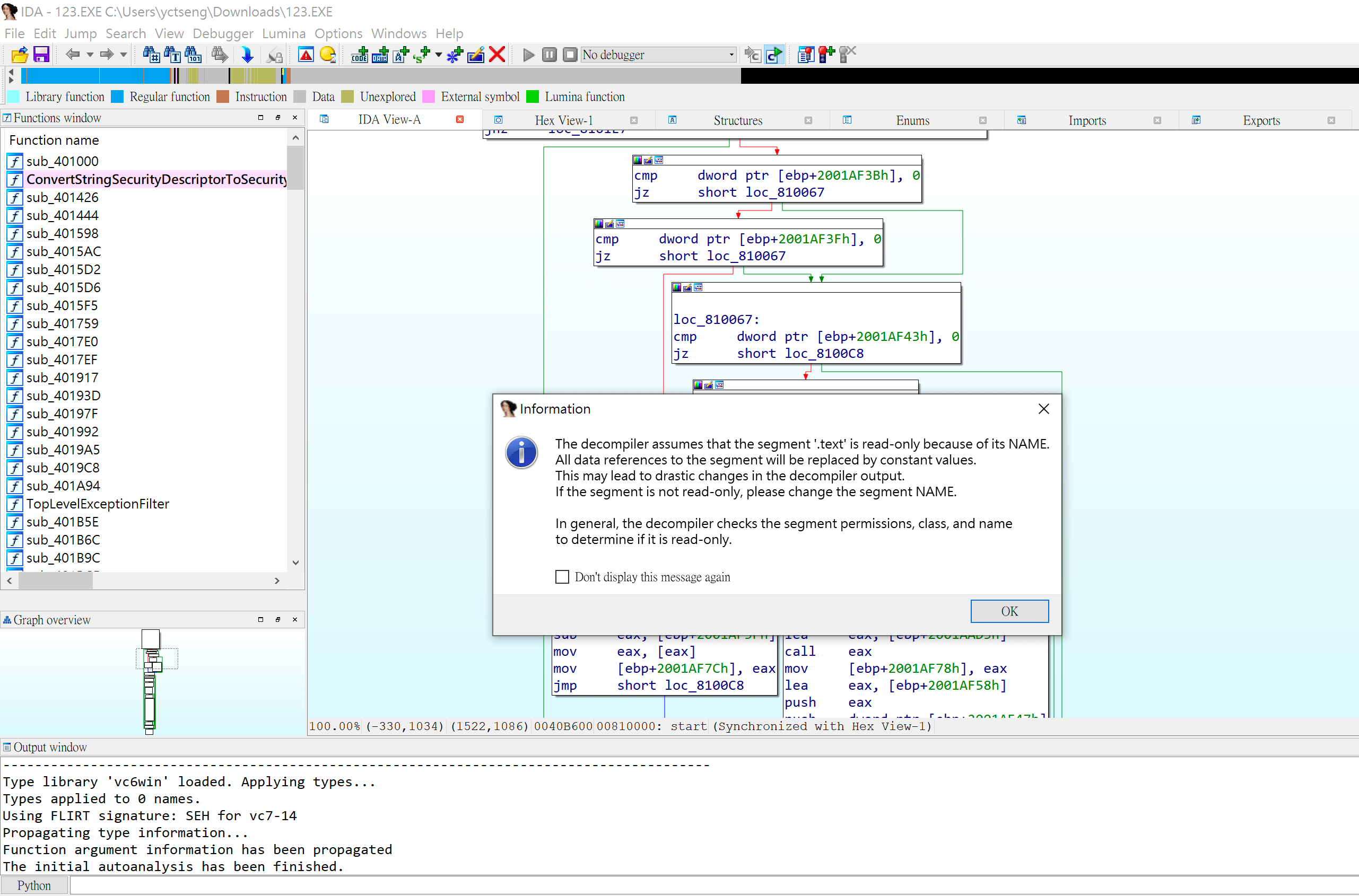
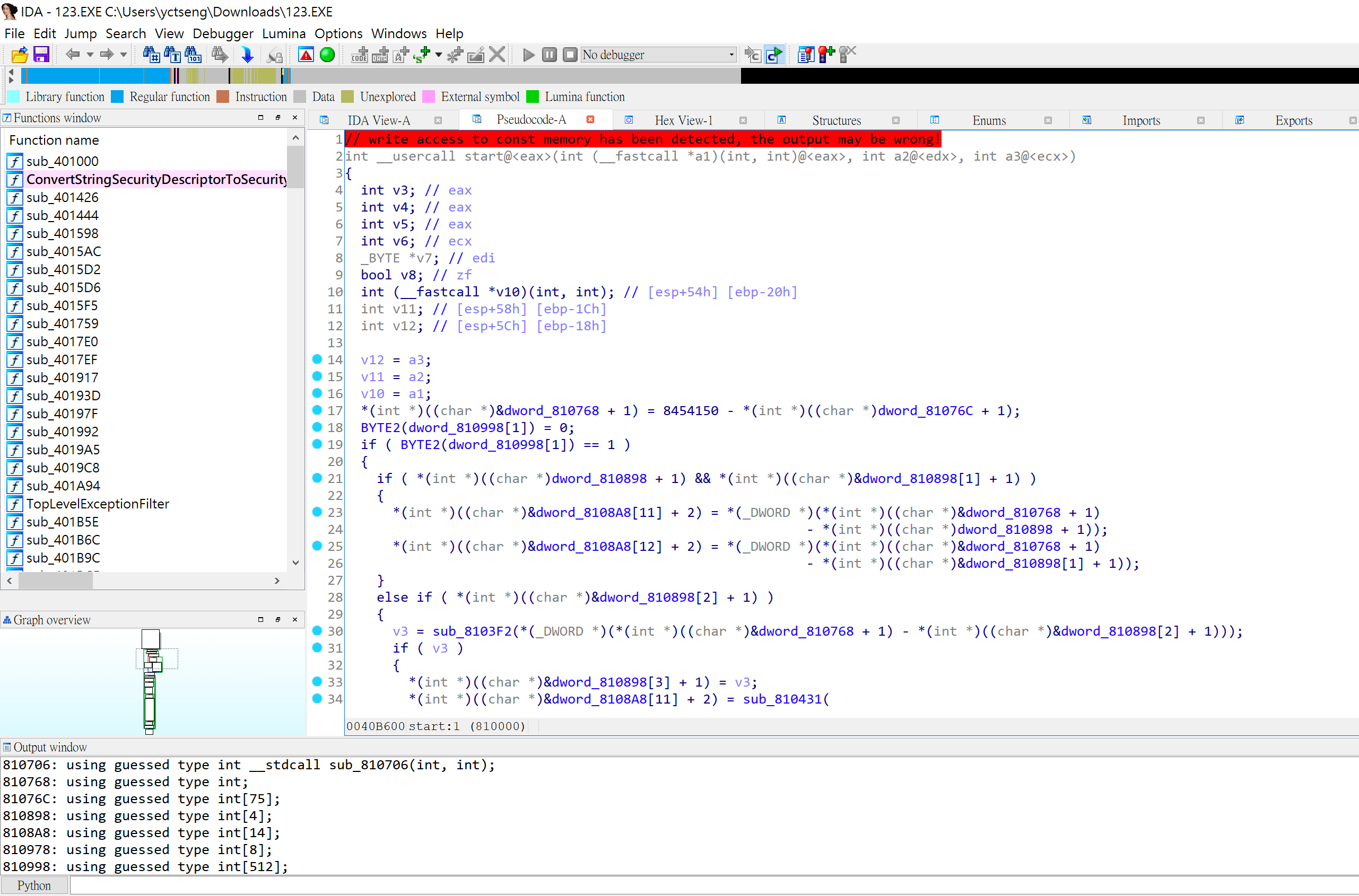
第一步,當然就是拿出逆向工程萬用寶具 IDA Pro 使用 F5 大法!


大概追了一小段時間… 嗯 看不懂呢QQ
該說組語的底子不夠嗎,雖然說很多 know-how / domain knowledge 需要 google (但我覺得就是自己沒耐心),本來還想用 x64dbg 下中斷點追一下細節,不過看起來是沒戲嗚嗚。
老實說,第一次這麼沒頭沒尾的就拿了檔案要分析,還真的不知道該做什麼w
CTF 好歹都有給情境或是至少不會毫無方向,所以就上網找了一下這類 Malware 分析的操作。
Regshot
首先是 Regshot,考慮到惡意程式通常會修改 registry,因此找到這個可以 snapshot 並且進行比較的開源程式。原本我的 sandbox 環境是在 Windows10 進行實驗,但是當我把比較的結果分享給 @stavhaygn 時,被提議使用 Windows7,一測下去 registry 的修改數量增加許多,原來目標主機的環境是 Windows7 早說嘛(雖然我自己也擅自預設環境為Win10)。
要說有什麼發現嗎?
很多註冊表的關鍵字要大概都一知半解,但可以注意到新增大量 ShellBags 的 key 和 value 企圖將 Malware 自己藏起來,話說連 {5C4F28B5-F869-4E84-8E60-F11DB97C5CC7} 這串 ID 都有東西可以查 XD,還有 FirewallPolicy 看起來都有被動到,最後 MuiCache 可以自定義 .exe 名稱顯示,這裡 Malware 看起來是偽裝成 Internet Explorer。
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
|
Regshot 1.9.0 x64 Unicode
Comments:
Datetime: -
Computer: -
Username: -
----------------------------------
Keys added: 4
----------------------------------
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\AppCompatFlags\Compatibility Assistant\Monitored
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\AppCompatFlags\Compatibility Assistant\Quarantined
HKU\S-1-5-21-2683313141-1501627848-3399458464-1000\Software\Cheat Engine
HKU\S-1-5-21-2683313141-1501627848-3399458464-1000\Software\Cheat Engine\Window Positions 96
----------------------------------
Values added: 14
----------------------------------
HKLM\SYSTEM\ControlSet001\services\SharedAccess\Parameters\FirewallPolicy\FirewallRules\TCP Query User{B722FD22-77FB-4A93-B73C-35A5003B8208}C:\program files (x86)\internet explorer\iexplore.exe: "v2.10|Action=Allow|Active=TRUE|Dir=In|Protocol=6|Profile=Public|App=C:\program files (x86)\internet explorer\iexplore.exe|Name=Internet Explorer|Desc=Internet Explorer|Defer=User|"
HKLM\SYSTEM\ControlSet001\services\SharedAccess\Parameters\FirewallPolicy\FirewallRules\UDP Query User{90FF74F6-3F69-4CB0-A8C9-B3478A25FFF5}C:\program files (x86)\internet explorer\iexplore.exe: "v2.10|Action=Allow|Active=TRUE|Dir=In|Protocol=17|Profile=Public|App=C:\program files (x86)\internet explorer\iexplore.exe|Name=Internet Explorer|Desc=Internet Explorer|Defer=User|"
HKLM\SYSTEM\CurrentControlSet\services\SharedAccess\Parameters\FirewallPolicy\FirewallRules\TCP Query User{B722FD22-77FB-4A93-B73C-35A5003B8208}C:\program files (x86)\internet explorer\iexplore.exe: "v2.10|Action=Allow|Active=TRUE|Dir=In|Protocol=6|Profile=Public|App=C:\program files (x86)\internet explorer\iexplore.exe|Name=Internet Explorer|Desc=Internet Explorer|Defer=User|"
HKLM\SYSTEM\CurrentControlSet\services\SharedAccess\Parameters\FirewallPolicy\FirewallRules\UDP Query User{90FF74F6-3F69-4CB0-A8C9-B3478A25FFF5}C:\program files (x86)\internet explorer\iexplore.exe: "v2.10|Action=Allow|Active=TRUE|Dir=In|Protocol=17|Profile=Public|App=C:\program files (x86)\internet explorer\iexplore.exe|Name=Internet Explorer|Desc=Internet Explorer|Defer=User|"
HKU\S-1-5-21-2683313141-1501627848-3399458464-1000\Software\Microsoft\Windows\CurrentVersion\Explorer\StartPage\StartMenu_Balloon_Time: C0 E1 E5 57 14 7E D7 01
HKU\S-1-5-21-2683313141-1501627848-3399458464-1000\Software\Microsoft\Windows\CurrentVersion\Explorer\UserAssist\{CEBFF5CD-ACE2-4F4F-9178-9926F41749EA}\Count\P:\Hfref\lpgfrat\Qbjaybnqf\0720 znyjner\znyjner\123.RKR: 00 00 00 00 01 00 00 00 00 00 00 00 00 00 00 00 00 00 80 BF 00 00 80 BF 00 00 80 BF 00 00 80 BF 00 00 80 BF 00 00 80 BF 00 00 80 BF 00 00 80 BF 00 00 80 BF 00 00 80 BF FF FF FF FF 10 BD 00 D6 13 7E D7 01 00 00 00 00
HKU\S-1-5-21-2683313141-1501627848-3399458464-1000\Software\Microsoft\Windows\CurrentVersion\Explorer\UserAssist\{CEBFF5CD-ACE2-4F4F-9178-9926F41749EA}\Count\P:\Hfref\lpgfrat\NccQngn\Ybpny\Grzc\prgenvaref\PRG7P55.gzc\rkgenpgrq\123.RKR: 00 00 00 00 00 00 00 00 03 00 00 00 2A F2 00 00 00 00 80 BF 00 00 80 BF 00 00 80 BF 00 00 80 BF 00 00 80 BF 00 00 80 BF 00 00 80 BF 00 00 80 BF 00 00 80 BF 00 00 80 BF FF FF FF FF 00 00 00 00 00 00 00 00 00 00 00 00
HKU\S-1-5-21-2683313141-1501627848-3399458464-1000\Software\Microsoft\Windows\CurrentVersion\Explorer\UserAssist\{CEBFF5CD-ACE2-4F4F-9178-9926F41749EA}\Count\{1NP14R77-02R7-4R5Q-O744-2RO1NR5198O7}\abgrcnq.rkr: 00 00 00 00 00 00 00 00 03 00 00 00 79 7D 01 00 00 00 80 BF 00 00 80 BF 00 00 80 BF 00 00 80 BF 00 00 80 BF 00 00 80 BF 00 00 80 BF 00 00 80 BF 00 00 80 BF 00 00 80 BF FF FF FF FF 00 00 00 00 00 00 00 00 00 00 00 00
HKU\S-1-5-21-2683313141-1501627848-3399458464-1000\Software\Classes\Local Settings\MuiCache\2\52C64B7E\@%SystemRoot%\System32\FirewallControlPanel.dll,-1: "Windows Firewall"
HKU\S-1-5-21-2683313141-1501627848-3399458464-1000\Software\Classes\Local Settings\Software\Microsoft\Windows\Shell\MuiCache\C:\program files (x86)\internet explorer\iexplore.exe: "Internet Explorer"
HKU\S-1-5-21-2683313141-1501627848-3399458464-1000\Software\Cheat Engine\Window Positions 96\AdvancedOptions Position: C0 00 00 00 00 01 00 00 3B 02 00 00 2F 01 00 00
HKU\S-1-5-21-2683313141-1501627848-3399458464-1000\Software\Cheat Engine\Window Positions 96\frmAutoInject Position: AE 01 00 00 E5 02 00 00 AF 01 00 00 4B 01 00 00
HKU\S-1-5-21-2683313141-1501627848-3399458464-1000_Classes\Local Settings\MuiCache\2\52C64B7E\@%SystemRoot%\System32\FirewallControlPanel.dll,-1: "Windows Firewall"
HKU\S-1-5-21-2683313141-1501627848-3399458464-1000_Classes\Local Settings\Software\Microsoft\Windows\Shell\MuiCache\C:\program files (x86)\internet explorer\iexplore.exe: "Internet Explorer"
----------------------------------
Values modified: 12
----------------------------------
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\ProfileList\S-1-5-21-2683313141-1501627848-3399458464-1000\RefCount: 0x00000004
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\ProfileList\S-1-5-21-2683313141-1501627848-3399458464-1000\RefCount: 0x00000005
HKLM\SOFTWARE\Wow6432Node\Microsoft\Windows NT\CurrentVersion\ProfileList\S-1-5-21-2683313141-1501627848-3399458464-1000\RefCount: 0x00000004
HKLM\SOFTWARE\Wow6432Node\Microsoft\Windows NT\CurrentVersion\ProfileList\S-1-5-21-2683313141-1501627848-3399458464-1000\RefCount: 0x00000005
HKLM\SYSTEM\ControlSet001\Control\Nsi\{eb004a03-9b1a-11d4-9123-0050047759bc}\24\ffffffffffffffffffffffffffffff01: 00 00 00 00 F2 00 00 00 02 00 00 00 FF FF FF FF FF FF FF FF FF FF FF FF
HKLM\SYSTEM\ControlSet001\Control\Nsi\{eb004a03-9b1a-11d4-9123-0050047759bc}\24\ffffffffffffffffffffffffffffff01: 00 00 00 00 F4 00 00 00 02 00 00 00 FF FF FF FF FF FF FF FF FF FF FF FF
HKLM\SYSTEM\ControlSet001\services\SharedAccess\Epoch\Epoch: 0x00000090
HKLM\SYSTEM\ControlSet001\services\SharedAccess\Epoch\Epoch: 0x00000098
HKLM\SYSTEM\CurrentControlSet\Control\Nsi\{eb004a03-9b1a-11d4-9123-0050047759bc}\24\ffffffffffffffffffffffffffffff01: 00 00 00 00 F2 00 00 00 02 00 00 00 FF FF FF FF FF FF FF FF FF FF FF FF
HKLM\SYSTEM\CurrentControlSet\Control\Nsi\{eb004a03-9b1a-11d4-9123-0050047759bc}\24\ffffffffffffffffffffffffffffff01: 00 00 00 00 F4 00 00 00 02 00 00 00 FF FF FF FF FF FF FF FF FF FF FF FF
HKLM\SYSTEM\CurrentControlSet\services\SharedAccess\Epoch\Epoch: 0x00000090
HKLM\SYSTEM\CurrentControlSet\services\SharedAccess\Epoch\Epoch: 0x00000098
HKU\S-1-5-21-2683313141-1501627848-3399458464-1000\Software\Microsoft\Windows\CurrentVersion\Explorer\UserAssist\{CEBFF5CD-ACE2-4F4F-9178-9926F41749EA}\Count\HRZR_PGYFRFFVBA: 00 00 00 00 64 00 00 00 8B 00 00 00 10 BF DA 00 0E 00 00 00 15 00 00 00 A0 68 06 00 4D 00 69 00 63 00 72 00 6F 00 73 00 6F 00 66 00 74 00 2E 00 57 00 69 00 6E 00 64 00 6F 00 77 00 73 00 2E 00 47 00 65 00 74 00 74 00 69 00 6E 00 67 00 53 00 74 00 61 00 72 00 74 00 65 00 64 00 00 00 00 00 01 00 00 00 00 00 00 00 F4 78 CE FE FE 07 00 00 90 00 00 00 00 00 00 00 54 D1 46 03 00 00 00 00 01 00 00 00 00 00 00 00 52 31 CE FE FE 07 00 00 02 00 00 00 00 00 00 00 A0 D1 46 03 00 00 00 00 E4 D7 46 03 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 DC 03 00 00 00 00 00 00 00 00 00 00 00 00 00 00 C0 D2 46 03 00 00 00 00 DC 03 00 00 00 00 00 00 C4 D2 46 03 00 00 00 00 00 00 00 00 00 00 00 00 98 BA BA FD FE 07 00 00 00 00 00 00 00 00 00 00 E0 A1 BA FD FE 07 00 00 00 00 00 00 00 00 00 00 80 D1 46 03 00 00 00 00 00 00 00
00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 20 05 39 00 00 00 00 00 7C 21 59 74 00 00 00 00 00 64 45 02 00 00 00 00 D0 CE 3A 00 00 00 00 00 00 00 00 00 00 00 00 00 F0 D3 46 03 00 00 00 00 50 E6 46 03 00 00 00 00 EC 3F 59 74 00 00 00 00 A0 79 33 00 00 00 00 00 30 D2 46 03 00 00 00 00 00 95 56 FD FE 07 00 00 E4 D7 46 03 00 00 00 00 00 00 00 00 00 00 00 00 98 77 A3 FE FE 07 00 00 00 00 00 00 00 00 00 00 74 D3 46 03 00 00 00 00 E4 D7 46 03 00 00 00 00 00 00 00 00 00 00 00 00 80 D3 46 03 00 00 00 00 80 D3 46 03 00 00 00 00 1D 47 10 77 00 00 00 00 2C 21 59 74 00 00 00 00 01 00 00 00 00 00 00 00 50 94 56 FD FE 07 00 00 00 00 00 00 00 00 00 00 01 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 02 00 00 00 00 00 00 00 02 00 00 00 0E 00 00 00 15 00 00 00 A0 68 06 00 4D 00 69 00 63 00 72 00 6F 00 73 00 6F 00 66 00 74 00 2E 00 57 00 69 00 6E 00 64 00 6F 00 77 00 73 00 2E 00 47 00 65 00 74 00 74 00 69 00 6E 00
67 00 53 00 74 00 61 00 72 00 74 00 65 00 64 00 00 00 00 00 01 00 00 00 00 00 00 00 F4 78 CE FE FE 07 00 00 90 00 00 00 00 00 00 00 54 D1 46 03 00 00 00 00 01 00 00 00 00 00 00 00 52 31 CE FE FE 07 00 00 02 00 00 00 00 00 00 00 A0 D1 46 03 00 00 00 00 E4 D7 46 03 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 DC 03 00 00 00 00 00 00 00 00 00 00 00 00 00 00 C0 D2 46 03 00 00 00 00 DC 03 00 00 00 00 00 00 C4 D2 46 03 00 00 00 00 00 00 00 00 00 00 00 00 98 BA BA FD FE 07 00 00 00 00 00 00 00 00 00 00 E0 A1 BA FD FE 07 00 00 00 00 00 00 00 00 00 00 80 D1 46 03 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 20 05 39 00 00 00 00 00 7C 21 59 74 00 00 00 00 00 64 45 02 00 00 00 00 D0 CE 3A 00 00 00 00 00 00 00 00 00 00 00 00 00 F0 D3 46 03 00 00 00 00 50 E6 46 03 00 00 00 00 EC 3F 59 74 00 00 00 00 A0 79 33 00 00 00 00 00 30 D2 46 03 00 00 00 00 00 95 56 FD FE 07 00 00 E4 D7 46 03 00 00 00 00 00 0
0 00 00 00 00 00 00 98 77 A3 FE FE 07 00 00 00 00 00 00 00 00 00 00 74 D3 46 03 00 00 00 00 E4 D7 46 03 00 00 00 00 00 00 00 00 00 00 00 00 80 D3 46 03 00 00 00 00 80 D3 46 03 00 00 00 00 1D 47 10 77 00 00 00 00 2C 21 59 74 00 00 00 00 01 00 00 00 00 00 00 00 50 94 56 FD FE 07 00 00 00 00 00 00 00 00 00 00 01 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 02 00 00 00 00 00 00 00 02 00 00 00 01 00 00 00 04 00 00 00 02 31 A9 00 43 00 3A 00 5C 00 55 00 73 00 65 00 72 00 73 00 5C 00 79 00 63 00 74 00 73 00 65 00 6E 00 67 00 5C 00 44 00 6F 00 77 00 6E 00 6C 00 6F 00 61 00 64 00 73 00 5C 00 70 00 72 00 6F 00 63 00 65 00 73 00 73 00 68 00 61 00 63 00 6B 00 65 00 72 00 2D 00 32 00 2E 00 33 00 39 00 2D 00 62 00 69 00 6E 00 5C 00 78 00 36 00 34 00 5C 00 50 00 72 00 6F 00 63 00 65 00 73 00 73 00 48 00 61 00 63 00 6B 00 65 00 72 00 2E 00 65 00 78 00 65 00 00 00 61 F2 51 41 00 00 00 00 00 00 00 00 C4 60 44 FD FE 07 00 00 00 00 00 00 00 00 00 00 A8 B2 F2 04 00 00 00 00 0C 80 80
FD FE 07 00 00 A8 B2 F2 04 00 00 00 00 01 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 01 00 00 00 06 00 00 00 EC D4 0B 00 7B 00 46 00 33 00 38 00 42 00 46 00 34 00 30 00 34 00 2D 00 31 00 44 00 34 00 33 00 2D 00 34 00 32 00 46 00 32 00 2D 00 39 00 33 00 A2 68 E6 76 00 00 00 00 37 00 44 00 45 00 30 00 42 00 32 00 38 00 46 00 43 00 32 00 33 00 7D 00 5C 00 65 00 78 00 70 00 60 58 A1 02 00 00 00 00 F9 25 85 FB FE 07 00 00 FF FF FF FF FF FF FF FF 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 20 E0 D7 02 00 00 00 00 42 89 C6 FE FE 07 00 00 44 E5 D7 02 00 00 00 00 59 03 C3 FE FE 07 00 00 48 E3 D7 02 00 00 00 00 47 50 4F 53 00 00 00 00 03 00 00 00 00 00 00 00 F9 25 85 FB FE 07 00 00 82 00 01 00 00 00 00 00 B8 00 01 00 00 00 00 00 50 B4 18 09 00 00 00 00 D3 F4 E5 76 00 00 00 00 01 00 00 02 00 00 00 00 B8 00 01 00 00 00 00 00 00 00 00 00 00 00 00 00 80 7A 2C 00 00 00 00 00 D8 E0 D7 02 00 00 00 00 7C 7C 2C 00 00 00 00 00 40 41 2D 00 00 00 00 00 20 00 00 00 00 00 00 00
00 00 00 00
HKU\S-1-5-21-2683313141-1501627848-3399458464-1000\Software\Microsoft\Windows\CurrentVersion\Explorer\UserAssist\{CEBFF5CD-ACE2-4F4F-9178-9926F41749EA}\Count\HRZR_PGYFRFFVBA: 00 00 00 00 65 00 00 00 9B 00 00 00 19 CC DE 00 0E 00 00 00 15 00 00 00 A0 68 06 00 4D 00 69 00 63 00 72 00 6F 00 73 00 6F 00 66 00 74 00 2E 00 57 00 69 00 6E 00 64 00 6F 00 77 00 73 00 2E 00 47 00 65 00 74 00 74 00 69 00 6E 00 67 00 53 00 74 00 61 00 72 00 74 00 65 00 64 00 00 00 00 00 01 00 00 00 00 00 00 00 F4 78 CE FE FE 07 00 00 90 00 00 00 00 00 00 00 54 D1 46 03 00 00 00 00 01 00 00 00 00 00 00 00 52 31 CE FE FE 07 00 00 02 00 00 00 00 00 00 00 A0 D1 46 03 00 00 00 00 E4 D7 46 03 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 DC 03 00 00 00 00 00 00 00 00 00 00 00 00 00 00 C0 D2 46 03 00 00 00 00 DC 03 00 00 00 00 00 00 C4 D2 46 03 00 00 00 00 00 00 00 00 00 00 00 00 98 BA BA FD FE 07 00 00 00 00 00 00 00 00 00 00 E0 A1 BA FD FE 07 00 00 00 00 00 00 00 00 00 00 80 D1 46 03 00 00 00 00 00 00 00
00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 20 05 39 00 00 00 00 00 7C 21 59 74 00 00 00 00 00 64 45 02 00 00 00 00 D0 CE 3A 00 00 00 00 00 00 00 00 00 00 00 00 00 F0 D3 46 03 00 00 00 00 50 E6 46 03 00 00 00 00 EC 3F 59 74 00 00 00 00 A0 79 33 00 00 00 00 00 30 D2 46 03 00 00 00 00 00 95 56 FD FE 07 00 00 E4 D7 46 03 00 00 00 00 00 00 00 00 00 00 00 00 98 77 A3 FE FE 07 00 00 00 00 00 00 00 00 00 00 74 D3 46 03 00 00 00 00 E4 D7 46 03 00 00 00 00 00 00 00 00 00 00 00 00 80 D3 46 03 00 00 00 00 80 D3 46 03 00 00 00 00 1D 47 10 77 00 00 00 00 2C 21 59 74 00 00 00 00 01 00 00 00 00 00 00 00 50 94 56 FD FE 07 00 00 00 00 00 00 00 00 00 00 01 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 02 00 00 00 00 00 00 00 02 00 00 00 0E 00 00 00 15 00 00 00 A0 68 06 00 4D 00 69 00 63 00 72 00 6F 00 73 00 6F 00 66 00 74 00 2E 00 57 00 69 00 6E 00 64 00 6F 00 77 00 73 00 2E 00 47 00 65 00 74 00 74 00 69 00 6E 00
67 00 53 00 74 00 61 00 72 00 74 00 65 00 64 00 00 00 00 00 01 00 00 00 00 00 00 00 F4 78 CE FE FE 07 00 00 90 00 00 00 00 00 00 00 54 D1 46 03 00 00 00 00 01 00 00 00 00 00 00 00 52 31 CE FE FE 07 00 00 02 00 00 00 00 00 00 00 A0 D1 46 03 00 00 00 00 E4 D7 46 03 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 DC 03 00 00 00 00 00 00 00 00 00 00 00 00 00 00 C0 D2 46 03 00 00 00 00 DC 03 00 00 00 00 00 00 C4 D2 46 03 00 00 00 00 00 00 00 00 00 00 00 00 98 BA BA FD FE 07 00 00 00 00 00 00 00 00 00 00 E0 A1 BA FD FE 07 00 00 00 00 00 00 00 00 00 00 80 D1 46 03 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 20 05 39 00 00 00 00 00 7C 21 59 74 00 00 00 00 00 64 45 02 00 00 00 00 D0 CE 3A 00 00 00 00 00 00 00 00 00 00 00 00 00 F0 D3 46 03 00 00 00 00 50 E6 46 03 00 00 00 00 EC 3F 59 74 00 00 00 00 A0 79 33 00 00 00 00 00 30 D2 46 03 00 00 00 00 00 95 56 FD FE 07 00 00 E4 D7 46 03 00 00 00 00 00 0
0 00 00 00 00 00 00 98 77 A3 FE FE 07 00 00 00 00 00 00 00 00 00 00 74 D3 46 03 00 00 00 00 E4 D7 46 03 00 00 00 00 00 00 00 00 00 00 00 00 80 D3 46 03 00 00 00 00 80 D3 46 03 00 00 00 00 1D 47 10 77 00 00 00 00 2C 21 59 74 00 00 00 00 01 00 00 00 00 00 00 00 50 94 56 FD FE 07 00 00 00 00 00 00 00 00 00 00 01 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 02 00 00 00 00 00 00 00 02 00 00 00 01 00 00 00 06 00 00 00 24 07 AA 00 43 00 3A 00 5C 00 55 00 73 00 65 00 72 00 73 00 5C 00 79 00 63 00 74 00 73 00 65 00 6E 00 67 00 5C 00 44 00 6F 00 77 00 6E 00 6C 00 6F 00 61 00 64 00 73 00 5C 00 70 00 72 00 6F 00 63 00 65 00 73 00 73 00 68 00 61 00 63 00 6B 00 65 00 72 00 2D 00 32 00 2E 00 33 00 39 00 2D 00 62 00 69 00 6E 00 5C 00 78 00 36 00 34 00 5C 00 50 00 72 00 6F 00 63 00 65 00 73 00 73 00 48 00 61 00 63 00 6B 00 65 00 72 00 2E 00 65 00 78 00 65 00 00 00 FE 07 00 00 00 00 00 00 00 00 00 00 80 7A 2C 00 00 00 00 00 50 BF 0F 04 00 00 00 00 A4 7C 2C 00 00 00 00 00 90 E8 2C
00 00 00 00 00 00 00 00 00 00 00 00 00 A0 DB FB 03 00 00 00 00 00 00 00 00 00 00 00 00 00 01 09 08 00 00 00 00 00 00 00 00 00 00 00 00 10 54 18 77 00 00 00 00 00 00 00 00 00 00 00 00 E0 00 00 00 00 00 00 00 00 00 2C 00 00 00 00 00 00 44 FF 03 00 00 00 00 A2 68 E6 76 00 00 00 00 58 03 2C 00 00 00 00 00 B5 EE 16 4C 2E C8 16 0E 3D E8 F2 66 45 7D 00 00 26 08 43 FD FE 07 00 00 00 00 00 00 00 00 00 00 9E 02 00 00 FE 07 00 00 00 00 00 00 FF FF FF FF 00 00 00 00 00 00 00 00 06 00 00 00 00 00 00 00 A8 38 D6 FF 00 00 00 00 20 E0 D7 02 00 00 00 00 42 89 C6 FE FE 07 00 00 44 E5 D7 02 00 00 00 00 59 03 C3 FE FE 07 00 00 48 E3 D7 02 00 00 00 00 47 50 4F 53 00 00 00 00 03 00 00 00 00 00 00 00 F9 25 85 FB FE 07 00 00 82 00 01 00 00 00 00 00 B8 00 01 00 00 00 00 00 01 00 00 02 00 00 00 00 20 00 00 00 00 00 00 00 01 00 00 02 00 00 00 00 B8 00 01 00 00 00 00 00 00 00 00 00 00 00 00 00 0E 76 E6 76 00 00 00 00 D8 E0 D7 02 00 00 00 00 7C 7C 2C 00 00 00 00 00 B8 00 01 00 00 00 00 00 20 00 00 00 00 00 00 00
00 00 00 00
HKU\S-1-5-21-2683313141-1501627848-3399458464-1000\Software\Microsoft\Windows\CurrentVersion\Explorer\UserAssist\{CEBFF5CD-ACE2-4F4F-9178-9926F41749EA}\Count\{S38OS404-1Q43-42S2-9305-67QR0O28SP23}\rkcybere.rkr: 00 00 00 00 01 00 00 00 0A 00 00 00 E8 36 0C 00 00 00 80 BF 00 00 80 BF 00 00 80 BF 00 00 80 BF 00 00 80 BF 00 00 80 BF 00 00 80 BF 00 00 80 BF 00 00 80 BF 00 00 80 BF FF FF FF FF C0 D0 80 42 46 7D D7 01 00 00 00 00
HKU\S-1-5-21-2683313141-1501627848-3399458464-1000\Software\Microsoft\Windows\CurrentVersion\Explorer\UserAssist\{CEBFF5CD-ACE2-4F4F-9178-9926F41749EA}\Count\{S38OS404-1Q43-42S2-9305-67QR0O28SP23}\rkcybere.rkr: 00 00 00 00 01 00 00 00 0F 00 00 00 77 76 0C 00 00 00 80 BF 00 00 80 BF 00 00 80 BF 00 00 80 BF 00 00 80 BF 00 00 80 BF 00 00 80 BF 00 00 80 BF 00 00 80 BF 00 00 80 BF FF FF FF FF C0 D0 80 42 46 7D D7 01 00 00 00 00
HKU\S-1-5-21-2683313141-1501627848-3399458464-1000\Software\Microsoft\Windows\CurrentVersion\Explorer\UserAssist\{CEBFF5CD-ACE2-4F4F-9178-9926F41749EA}\Count\P:\Hfref\lpgfrat\Qbjaybnqf\cebprffunpxre-2.39-ova\k64\CebprffUnpxre.rkr: 00 00 00 00 01 00 00 00 04 00 00 00 02 31 A9 00 00 00 80 BF 00 00 80 BF 00 00 80 BF 00 00 80 BF 00 00 80 BF 00 00 80 BF 00 00 80 BF 00 00 80 BF 00 00 80 BF 00 00 80 BF FF FF FF FF 90 C6 6B 48 99 7D D7 01 00 00 00 00
HKU\S-1-5-21-2683313141-1501627848-3399458464-1000\Software\Microsoft\Windows\CurrentVersion\Explorer\UserAssist\{CEBFF5CD-ACE2-4F4F-9178-9926F41749EA}\Count\P:\Hfref\lpgfrat\Qbjaybnqf\cebprffunpxre-2.39-ova\k64\CebprffUnpxre.rkr: 00 00 00 00 01 00 00 00 06 00 00 00 24 07 AA 00 00 00 80 BF 00 00 80 BF 00 00 80 BF 00 00 80 BF 00 00 80 BF 00 00 80 BF 00 00 80 BF 00 00 80 BF 00 00 80 BF 00 00 80 BF FF FF FF FF 90 C6 6B 48 99 7D D7 01 00 00 00 00
HKU\S-1-5-21-2683313141-1501627848-3399458464-1000\Software\Microsoft\Windows\CurrentVersion\Explorer\UserAssist\{CEBFF5CD-ACE2-4F4F-9178-9926F41749EA}\Count\P:\Hfref\lpgfrat\Qbjaybnqf\Ertfubg-1.9.0\Ertfubg-k64-Havpbqr.rkr: 00 00 00 00 01 00 00 00 00 00 00 00 00 00 00 00 00 00 80 BF 00 00 80 BF 00 00 80 BF 00 00 80 BF 00 00 80 BF 00 00 80 BF 00 00 80 BF 00 00 80 BF 00 00 80 BF 00 00 80 BF FF FF FF FF 00 3C 16 C0 13 7E D7 01 00 00 00 00
HKU\S-1-5-21-2683313141-1501627848-3399458464-1000\Software\Microsoft\Windows\CurrentVersion\Explorer\UserAssist\{CEBFF5CD-ACE2-4F4F-9178-9926F41749EA}\Count\P:\Hfref\lpgfrat\Qbjaybnqf\Ertfubg-1.9.0\Ertfubg-k64-Havpbqr.rkr: 00 00 00 00 01 00 00 00 03 00 00 00 B5 87 00 00 00 00 80 BF 00 00 80 BF 00 00 80 BF 00 00 80 BF 00 00 80 BF 00 00 80 BF 00 00 80 BF 00 00 80 BF 00 00 80 BF 00 00 80 BF FF FF FF FF 00 3C 16 C0 13 7E D7 01 00 00 00 00
HKU\S-1-5-21-2683313141-1501627848-3399458464-1000\Software\Classes\Local Settings\Software\Microsoft\Windows\Shell\BagMRU\2\0\MRUListEx: 03 00 00 00 00 00 00 00 02 00 00 00 01 00 00 00 FF FF FF FF
HKU\S-1-5-21-2683313141-1501627848-3399458464-1000\Software\Classes\Local Settings\Software\Microsoft\Windows\Shell\BagMRU\2\0\MRUListEx: 00 00 00 00 03 00 00 00 02 00 00 00 01 00 00 00 FF FF FF FF
HKU\S-1-5-21-2683313141-1501627848-3399458464-1000_Classes\Local Settings\Software\Microsoft\Windows\Shell\BagMRU\2\0\MRUListEx: 03 00 00 00 00 00 00 00 02 00 00 00 01 00 00 00 FF FF FF FF
HKU\S-1-5-21-2683313141-1501627848-3399458464-1000_Classes\Local Settings\Software\Microsoft\Windows\Shell\BagMRU\2\0\MRUListEx: 00 00 00 00 03 00 00 00 02 00 00 00 01 00 00 00 FF FF FF FF
----------------------------------
Total changes: 30
----------------------------------
|
雖然沒有實際測過,但修改的 registry 我猜也包含重開機自動 RUN 起來吧,剩下的真要認真查可能要不少時間,所以我只有找了幾個有興趣的關鍵字稍微摸過。
Process Hacker
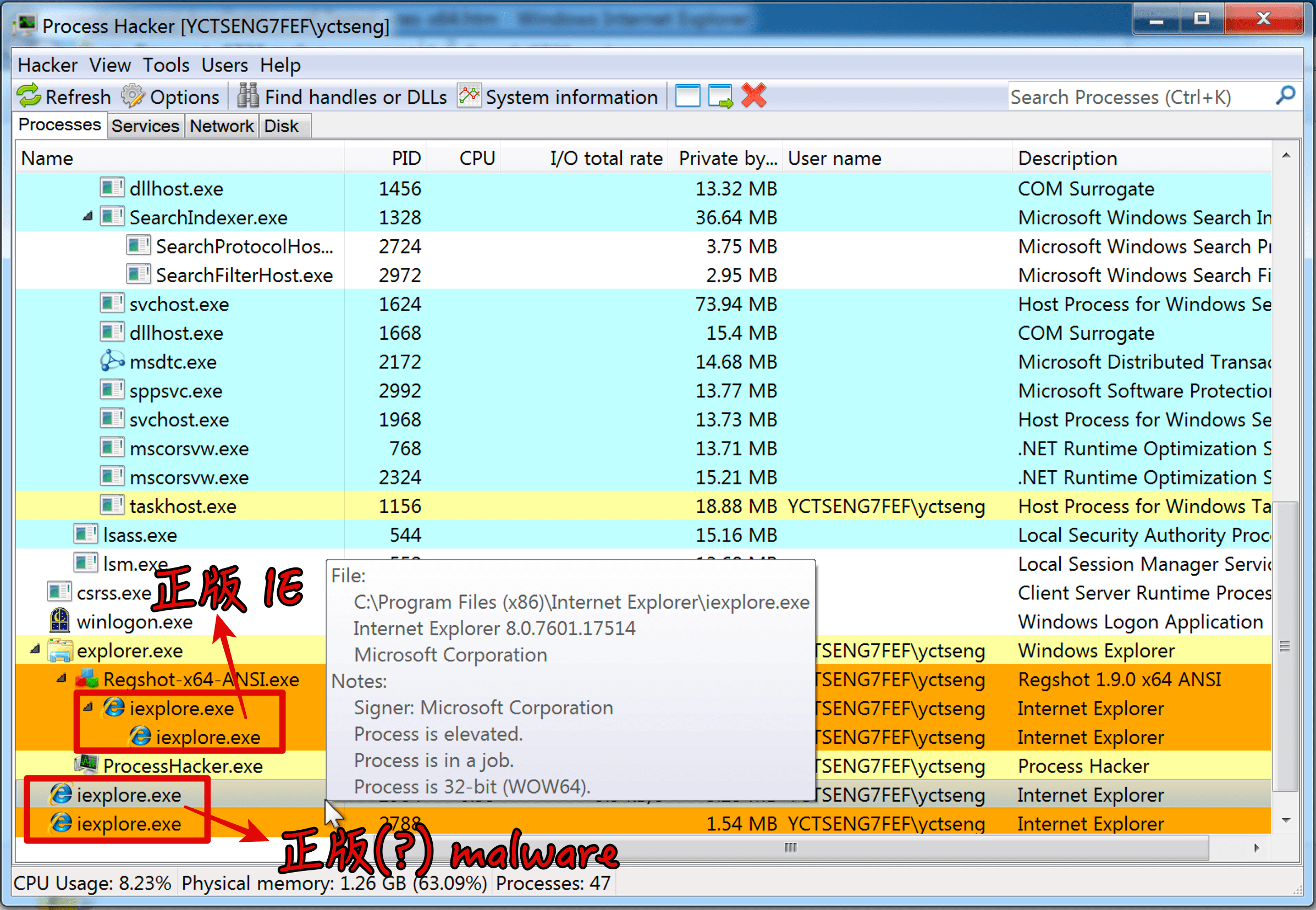
Process Hacker 簡單講就是工作管理員的進階版(O),平常沒碰 Windows 的我也是問了才知道有這軟體可以進一步觀察 process 在後台執行的狀況。
將 Malware RUN 起來,出現模仿相當完美的 IE,只是出現位置不對(笑)

原本在斷網的 Sandbox 等不到 Malware 發 request,所以只好手機開分享看看他會怎麼運作,抓到程式連到 Amazon EC2 的行為(經驗判斷應該是連 C2 Server,是常見的 Botnet 手法)。

順便宣導一下 !!!不要走學校網路,除非想收資安通報!!!
不過後續不清楚 Malware 怎麼運作,就只是反覆一直連線,看到 Network 那一坨 domain 又不清掉實在讓人略不爽(?)

最後,發現在 kill 掉 Malware 後過沒多久會自己重啟(怕.jpg)
Wireshark
Wireshark 是用來分析網路封包的工具。
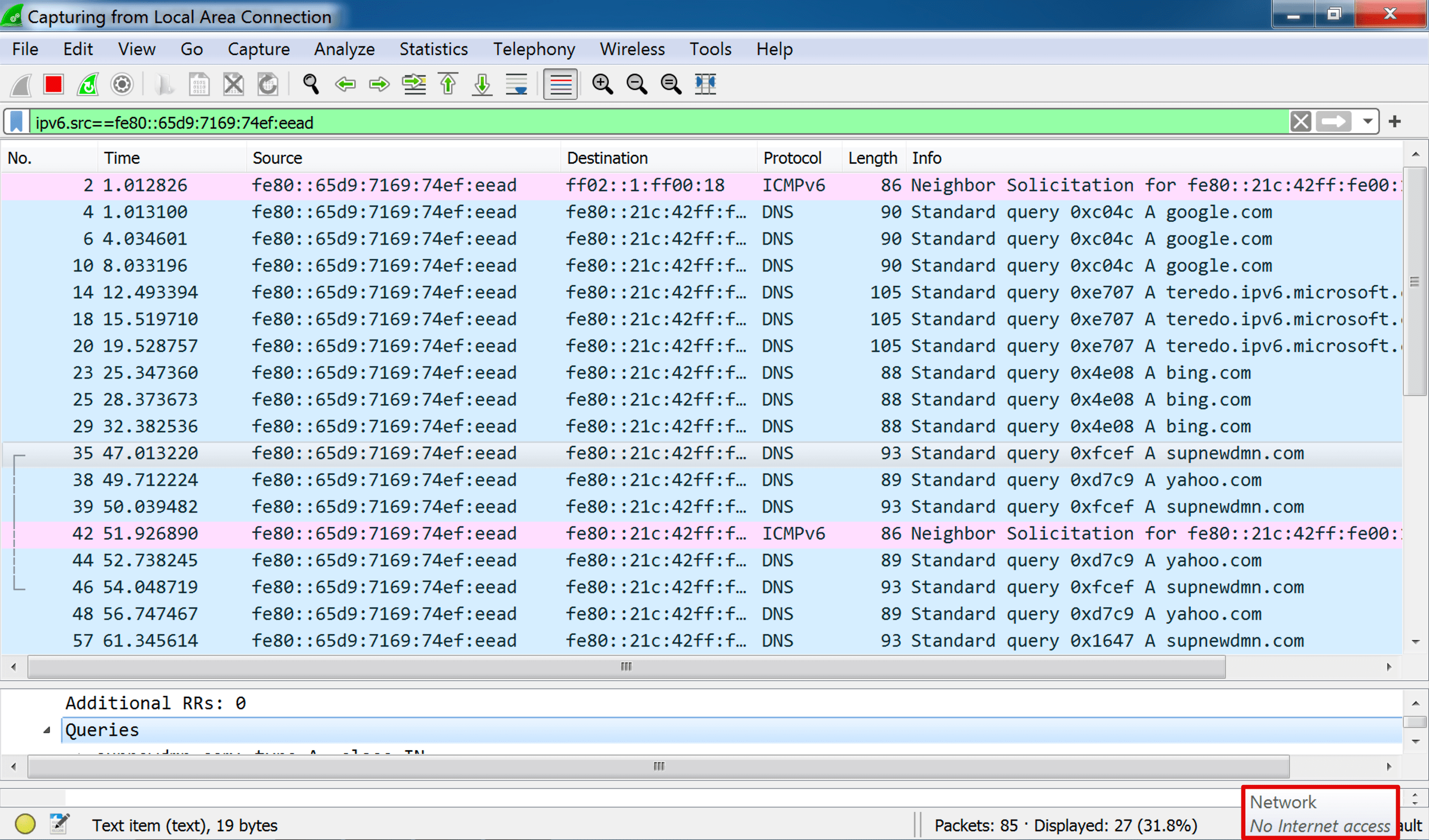
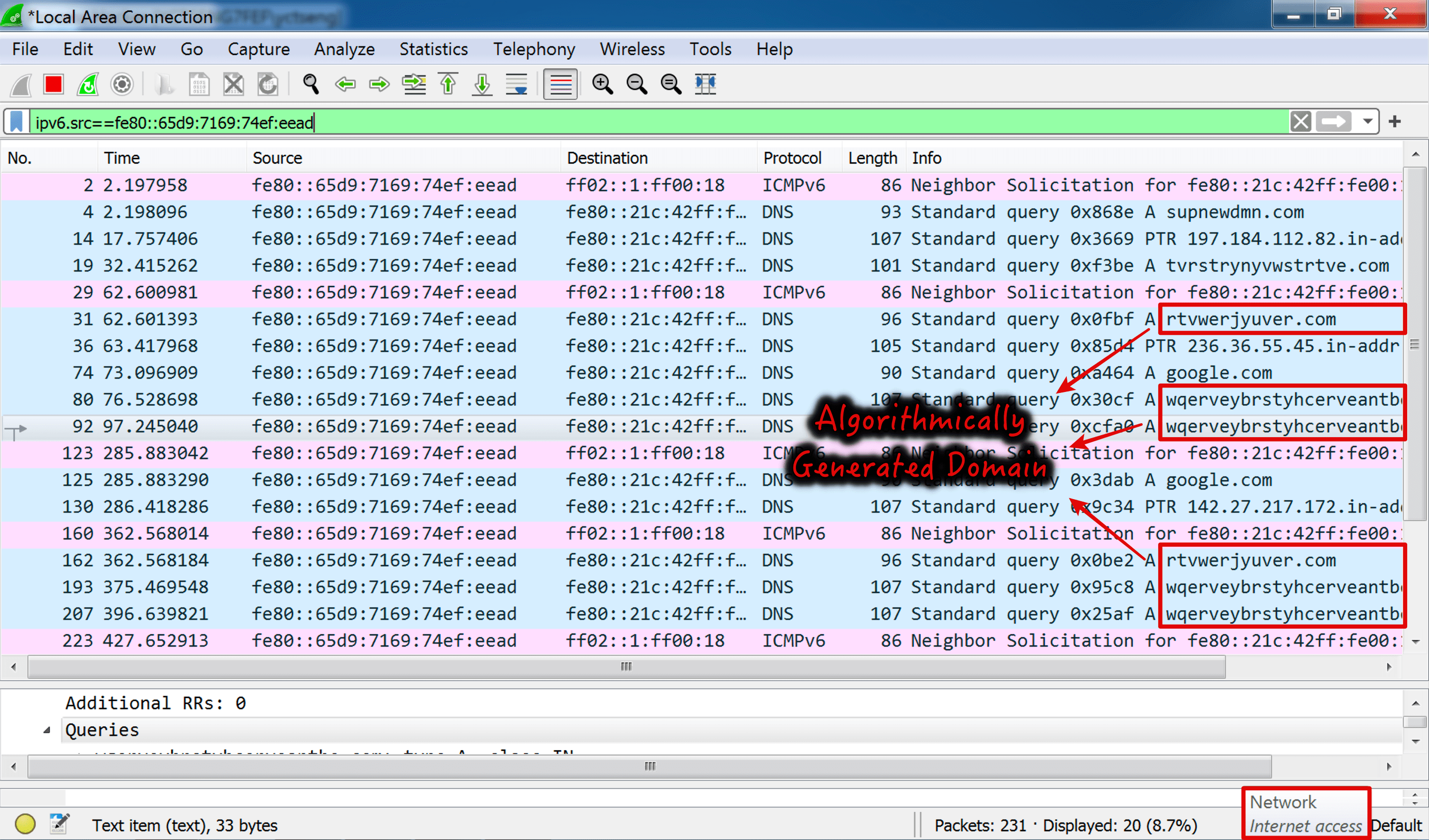
原本在斷網環境錄製封包一直沒有看到預期的 request,猜想 Malware 是否有判斷網路環境,所以我用手機開網路分享(但不對外開行動網路),發現在 DNS 開始會有 google.com、yahoo.com、bing.com 的詢問,但還有一個 supnewdmn[.]com 的 DNS 詢問,從 VirusTotal 的回報比例有 12/87,沒意外是惡意網域,之後會有一些看起來是 DGA 產生的 random domain name應該就是用來連上 Amazon EC2,也就是方才提到的 C2 Server。


直接對外連網後,DNS 查詢的 domain 就會限縮到 google.com 和 supnewdmn[.]com,以及 random domain name。從 Process Hacker 得知的連線 Port 447 來看,由於封包都是走 TCP,所以從 Wireshark 看不到什麼內容 QQ
CAPE Sandbox
CAPE Sandbox 是去年 Still 在社課分享的線上 Malware sandbox,我也藉這次機會分別把 malware-A 和 malware-B 丟上去,有興趣的可以上去看看分析報告。
In the End …
從分析 Malware 的時候不難看出該程式的原型是 cheat engine,只是被加料了 (下圖借用 CAPE Sandbox Screenshot)。

而故事的後續,原來是 @stavhaygn 友人透過 VPN 走校園網路,結果下載的私服外掛被埋了蠕蟲,因此校方 IPS 在分析惡意流量追溯 IP 才會追到我們 Lab 的伺服器,這件事告訴我們 慎選朋友 使用學校網路請不要壞壞。
最後,簡單畫個這次分析的示意圖吧,只是 Malware 到底從 C2 server 那邊拿了什麼做了什麼,就不知道了 QwQ 但我想下一步從 reverse 著手應該會有進一步地發現。